

Who decides what “truth” is? In concept I’m with you but in practice that sounds like a nightmare. See: mainland china
Governments should be the arbiters of law and recommendations, not the arbiters of truth.


Who decides what “truth” is? In concept I’m with you but in practice that sounds like a nightmare. See: mainland china
Governments should be the arbiters of law and recommendations, not the arbiters of truth.

The state of modern technology is so unhinged that not only has it been a basic feature of the core operating system for almost a decade, enabling it on any device that doesn’t intentionally break the feature is literally just creating a specific text file with the desired charge limit as an integer.
echo "80" > /sys/devices/platform/google,charger/charge_stop_level
I wish we owned the things we bought. 🙃


King size candy bars, give out 2 to each. Everyone always loved that guy


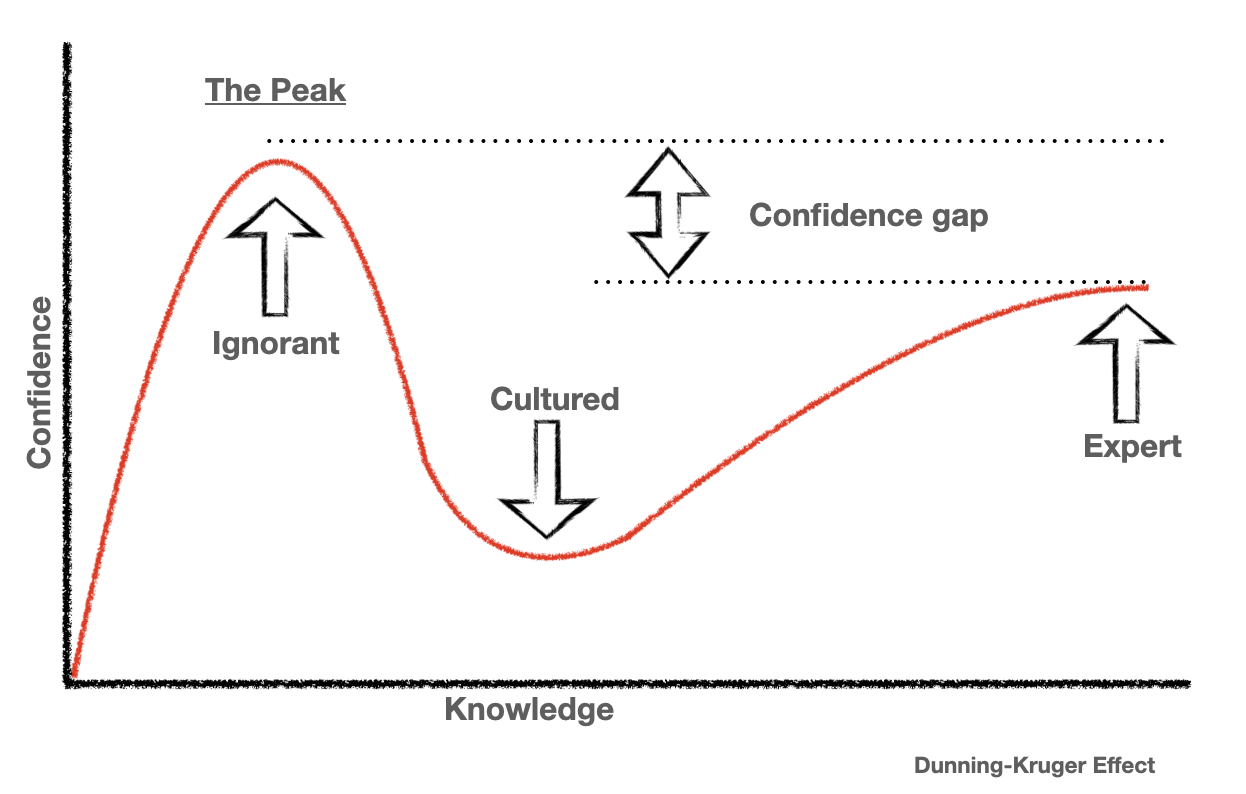
The thing about rational actors, is when given the same information they should make the same choices. I would argue that they’re most likely, instead, just at the peak of mt. stupid


We shouldn’t blame the victims that society failed to properly educate. You’re right that if people intimately understood apple the way you probably do, they’d never buy an apple product. I would argue, however, that it’s a failing of education not an informed choice to be corporately cucked.


Noooo, you got this backwards. Think about how many times you wanted an extra key for something. Push-to-talk in VoIP apps, extra modifier keys so you don’t have to use double-modifiers… The possibilities are endless!
Standardize more useless keys so I can remap them on every keyboard!


I don’t think anyone should expect a battery replacement to be free after 10 years, but it shouldn’t cost $100,000
Just because you can’t use it doesn’t mean a hacker can’t. If someone discovered a vulnerability in the 3g handshake or encryption protocol, it could be an avenue for an RCE.


the best way to learn is by doing!


I just built my own automation around their official documentation; it’s fantastic.
https://www.wireguard.com/#conceptual-overview


vyatta and vyatta-based (edgerouter, etc) I would say are good enough for the average consumer. If we’re deep enough in the weeds to be arguing the pros and cons of wireguard raw vs talescale; I think we’re certainly passed accepting a budget consumer router as acceptably meeting these and other needs.
Also you don’t need port forwarding and ddns for internal routing. My phone and laptop both have automation in place for switching wireguard profiles based on network SSID. At home, all traffic is routed locally; outside of my network everything goes through ddns/port forwarding.
If you’re really paranoid about it, you could always skip the port-forward route, and set up a wireguard-based mesh yourself using an external vps as a relay. That way you don’t have to open anything directly, and internal traffic still routes when you don’t have an internet connection at home. It’s basically what talescale is, except in this case you control the keys and have better insight into who is using them, and you reverse the authentication paradigm from external to internal.


Talescale proper gives you an external dependency (and a lot of security risk), but the underlying technology (wireguard) does not have the same limitation. You should just deploy wireguard yourself; it’s not as scary as it sounds.


Fail2ban and containers can be tricky, because under the hood, you’ll often have container policies automatically inserting themselves above host policies in iptables. The docker documentation has a good write-up on how to solve it for their implementation
https://docs.docker.com/engine/network/packet-filtering-firewalls/
For your usecase specifically: If you’re using VMs only, you could run it within any VM that is exposing traffic, but for containers you’ll have to run fail2ban on the host itself. I’m not sure how LXC handles this, but I assume it’s probably similar to docker.
The simplest solution would be to just put something between your hypervisor and the Internet physically (a raspberry-pi-based firewall, etc)


Devil’s Advocate:
How do we know that our brains don’t work the same way?
Why would it matter that we learn differently than a program learns?
Suppose someone has a photographic memory, should it be illegal for them to consume copyrighted works?
It’s fuckin’ art though


Oracle, SAP, Redhat, all of their customer portals require it for SSO. I’m not saying it should be that way, but it is.


I think you go about it the other way: break data analytics and advertising off from everything else. If every unit has to be self-sufficient without reliance on data collection and first-party advertising I think you fix most of the major issues.


I’m actually working on a vector DB RAG system for my own documentation. Even in its rudimentary stages, it’s been very helpful for finding functions in my own code that I don’t remember exactly what project I implemented it in, but have a vague idea what it did.
E.g
Have I ever written a bash function that orders non-symver GitHub branches?
Yes! In your ‘webwork automation’ project, starting on line 234, you wrote a function that sorts Git branches based on WebWork’s versioning conventions.


I’m sorry but this is just a fundamentally incorrect take on the physics at play here.
You unfortunately can’t ever prevent further breakdown. Every time you run any voltage through any CPU, you are always slowly breaking down gate-oxides. This is a normal, non-thermal failure mode of consumer CPUs. The issue is that this breakdown is non-linear. As the breakdown process increases, it increases resistance inside the die, and as a consequence requires higher minimum voltages to remain stable. That higher voltage accelerates the rate of idle damage, making time disproportionately more damaging the more damaged a chip is.
If you want to read more on these failure modes, I’d recommend the following papers:
L. Shi et al., “Effects of Oxide Electric Field Stress on the Gate Oxide Reliability of Commercial SiC Power MOSFETs,” 2022 IEEE 9th Workshop on Wide Bandgap Power Devices & Applications
Y. Qian et al., “Modeling of Hot Carrier Injection on Gate-Induced Drain Leakage in PDSOI nMOSFET,” 2021 IEEE International Conference on Integrated Circuits, Technologies and Applications
This is probably the play they’re making; the only thing that makes me think it might be something else is that they also announced ditching proprietary code in favor of kvm in workstation. Makes me wonder if they instead are deciding to slowly kill the product line, and instead of just stopping development entirely, they’re giving it out as if it’s some huge gift to try and “buy” good will before it becomes an inferior product?
Either way, support costs for the product are now $0 (because you can’t buy it) and development costs are about to be near-zero if they’re forking upstream kvm.
https://www.phoronix.com/news/VMware-Workstation-KVM